The Checkup Report tab of Archive Manager Properties page may be configured to send the checkup report using encrypted email via the TLS version 1 protocol. If desired, encryption can be enabled using TLS version 1.2.
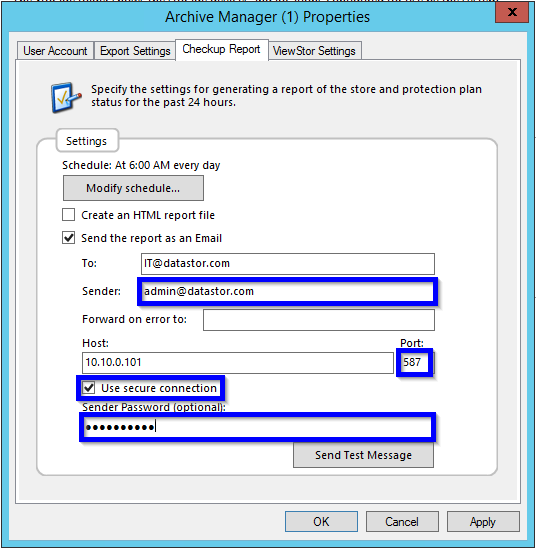
An SMTP server will accept email using TLS version 1 using the following settings on the Checkup Report tab of the Archive Manager properties page:
Sender: [a valid email address]
Port: 587
Use secure connection checkbox checked
Sender Password (optional): [password entered]
To send the checkup report using TLS version 1.2 instead, set the checkup report settings above, and then follow these additional steps to enable TLSv1.2 on the computer hosting the software.
1. Check the version of .NET Framework installed on the computer. NET Framework 4.6.2 and later versions support TLS 1.1 and TLS 1.2. If needed, download and install a version of .NET Framework that supports TLS 1.1 and TLS 1.2 Downloads available here: https://dotnet.microsoft.com/download/dotnet-framework For more information, refer to the KB linked below. Important: Leave .NET Framework 3.5 installed. The DATASTOR software depends upon this installation, which includes .NET Framework 2.0.
2. If running Windows 2012, Windows 7 or an earlier operating system, enable WINHTTP. This step follows the KB linked below in the section "Update Windows and WinHTTP". Copy the registry entry below:
Windows Registry Editor Version 5.00
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\
DefaultSecureProtocols = (DWORD): 0xAA0
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\
DefaultSecureProtocols = (DWORD): 0xAA0Paste the entry into notepad and save with a .REG extension to create a standard REG file. Double click the file to import the entries. For 2012 R2 and later operating systems, this step is not required.
3. Configure strong cryptography. Again, just use the REG entries in the KB, or copy them below.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001Paste the entry into notepad and save with a .REG extension to create a standard REG file. Double click the file to import the entries.
4. Reboot
Reference Microsoft KB https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/security/enable-tls-1-2-client
A packet sniffing application may be used to confirm communication with an SMTP server on port 587 using protocol TLSv1.2,